The latest version of SAP Cloud Platform – Identity Access Governance (IAG) now provides the capability to analyze supply chain risks and provision access to SAP Ariba, providing governance of end-to-end cross system supply chain processes. This blog will explain how the cross-system risk analysis is performed and possible ways of connecting your SAP Ariba to either Cloud IAG standalone or using Cloud IAG with on-premise SAP Access Control.
Currently, on premise SAP Access Control does not have capabilities to connect to cloud applications. For this reason, SAP invested in a cloud solution called Identity Access Governance (IAG). The application does not replace Access Control which is still SAP’s flagship tool. The idea is to provide a SaaS (Software as a Service) application in SAP`s Cloud Platform to close the gap on access risk in SAP’s cloud products.
Architecture
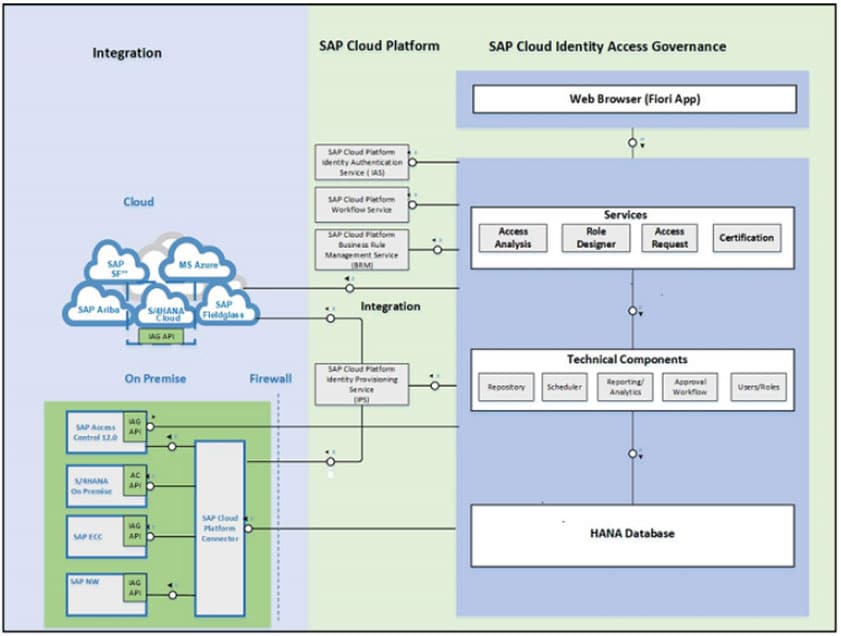
Identity Access Governance works with a multi-tenancy architecture. Each one of the customers has tenant and each tenant`s data is isolated and invisible to others.
Not all components of the diagram are needed. The details of each component are described in the table below. The integration from IAG to target applications is performed using SAP Cloud Connector.
| Component | Description |
|---|
Component | Description |
|---|---|
| Target Applications (on-Premise, cloud) | IAG can connect to both cloud and on premise applications (using Cloud Connector). |
| SAP Cloud Platform connector | The cloud connector sits behind the firewall and establishes connectivity between the SAP Cloud Platform and the target system. |
| IAG Services | · Access Analysis · Access Request · Role Design · Access Certification |
| IAG Technical Components | IAG enablement tools: · Repository · Scheduler · Reporting and Analytics · Approval Workflow · Users and Roles |
| SAP Cloud Platform Identity Authentication service | Identity Authentication (IAS) is a service located in Cloud Platform to authenticate users. User Authentication IAG solution and its services use SAP Cloud Platform Identity Authentication Service (IAS) for user authentication and to manage access to IAG apps. Security and permissions are maintained in groups and roles. You control the tasks a user can perform, and the apps they can access, through the appropriate assignment of group and role combinations to the user. 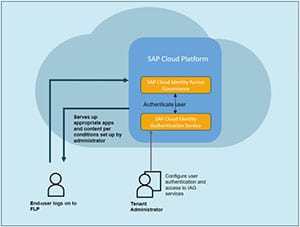 |
| SAP Cloud Platform Workflow service | Workflow service is used in the access request engine for automation of access requests through the various stages of creation and approval. |
| SAP Cloud Platform Business Rules service | Business Rules service enables embedding business decisions into the workflow. It acts as a BRFPlus on Cloud. The approvers and workflow initiators have to be defined in the Business Rules Service using predefined decision tables. |
| SAP Cloud Platform Identity Provisioning service | Identity Provisioning service allows provisioning of centrally managed identities and their access across the enterprise (on-premise and cloud). |
Services Available
The solution is built on the Cloud Platform. It can retrieve data from Cloud and on-premise solutions and enable users to create requests, analyse risks in real-time and design business roles. Also, the access certification allows you to review cloud user access from time to time to ensure compliance.
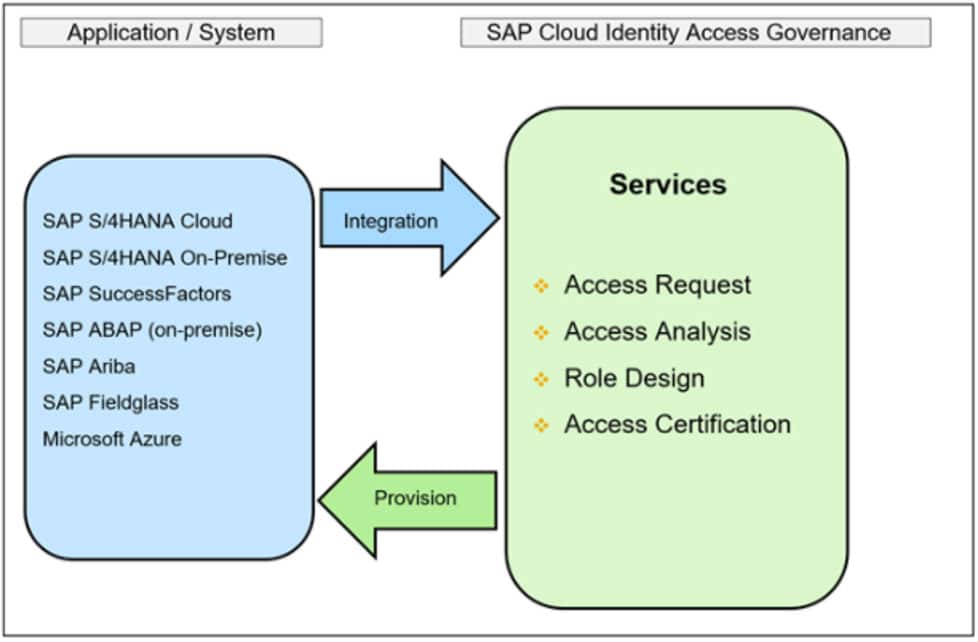
In Cloud Platform, systems are created to connect cloud applications to IAG. For Ariba, a system type of SAP Ariba must be created.
After this step is completed, the job to synchronize user data can be scheduled. It works like a repository synch and it synchs relevant information to start the provisioning process to Ariba.
Supply Chain Management and IAG
Real-time visibility is available for Ariba users and permissions with Identity Access Governance.
SAP Cloud Identity Access Governance subscribers can include access to SAP Ariba cloud solutions for buyers in their global identity and access management framework. Buyers using SAP Ariba cloud solutions can adopt the identity and access management capabilities of SAP Cloud Identity Access Governance to manage user access to SAP Ariba cloud solutions.
- Simplified governance of data access, with real-time, dashboard-driven analysis, insights, and audit reporting, for more productivity, visibility, and decision support
- Minimized access risk, non-compliance, and financial loss
- Configurable, predefined access policies and rules for governance enforcement
- Seamless user experience across all your solutions, whether from SAP Ariba or other companies
What is cross system risk?
Cross System risk analysis is used for scenarios where the access to an action or permission in one system conflicts with the access to an action or permission in another system. In a hybrid environment, it is the ability to start a transaction from on premise and finalize on cloud apps or vice versa.
What is the financial impact of an access risk incident in your supply chain processes?
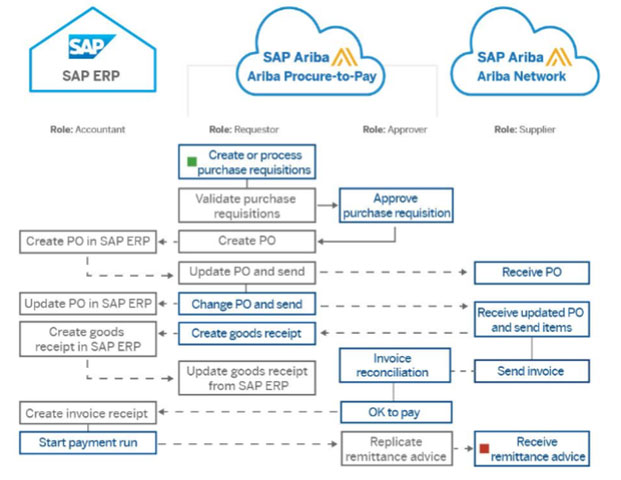
In the example above, the flow describes a purchase to pay process. The process is shared between Ariba and ECC or S/4HANA, depending on the integration scenario. Based on that, IAG comes with a comprehensive ruleset for cross system analysis. The example below is fictitious but gives an idea about how cross system rules are established for this business process.
| Cross System Risk | Function Definition | System | Actions |
|---|
Cross System Risk | Function Definition | System | Actions |
|---|---|---|---|
| ARIBA_001 - Approve Invoice and Pay Vendor | ARI01 – Approve Invoice | Ariba Approver | Ariba-approve |
| ARIBA_001 - Approve Invoice and Pay Vendor | ARI02 – Create Payment | ECC or S/4HANA | F110 |
SAP gives access to the ruleset via OSS. An incident has to be raised by IAG customers.
SAP IAG Bridge Integration
In organizations challenged with managing compliance across on-premise systems and cloud, additional processes and manual intervention are a reality. If operating in silos, an extension of Access Request, Risk Analysis and Business Role Management for cloud applications connects the landscape and aggregates value from both ends.
SAP offers an integration point from on premise Access Control to Identity Access Governance. Using the integration, on premise system compliance and cloud application compliance are combined.
Benefits
This cloud solution for Identity and Access Governance includes scheduled updates automatically. IAG aggregates with the on-premise solution and depending on the business requirements, it can be defined as the primary IAM tool.



