Introduction
Identity and Access Management (IAM) is one of the pillars for cybersecurity strategy today and companies are more aware of the importance of managing identities in their systems landscape to avoid potential cyber threats. There are many IAM products available in the market, flexing their unique capabilities to stand apart from one another. Each product is owned and developed by a ‘Product Owner’, and they are trying their best to make theirs more efficient at the cost of encroaching into other product functionalities. Hence creating multiple products doing similar features.
Often companies going through Transformation Programs are indecisive about which product they should adopt for their landscape. Typical questions clients ask include:
- Which product should I choose for our hybrid landscape?
- What’s the difference between Product A and B?
- Can we use SAP products to setup Enterprise IAM solution for SAP identity provisioning?
- Can Product A support Cloud Provisioning?
In this multiple blog series, we will do a comparative analysis of SAP IAM products, provide in-depth analysis of each product and guide you to choose a product which best fits your organisation.
Analysis
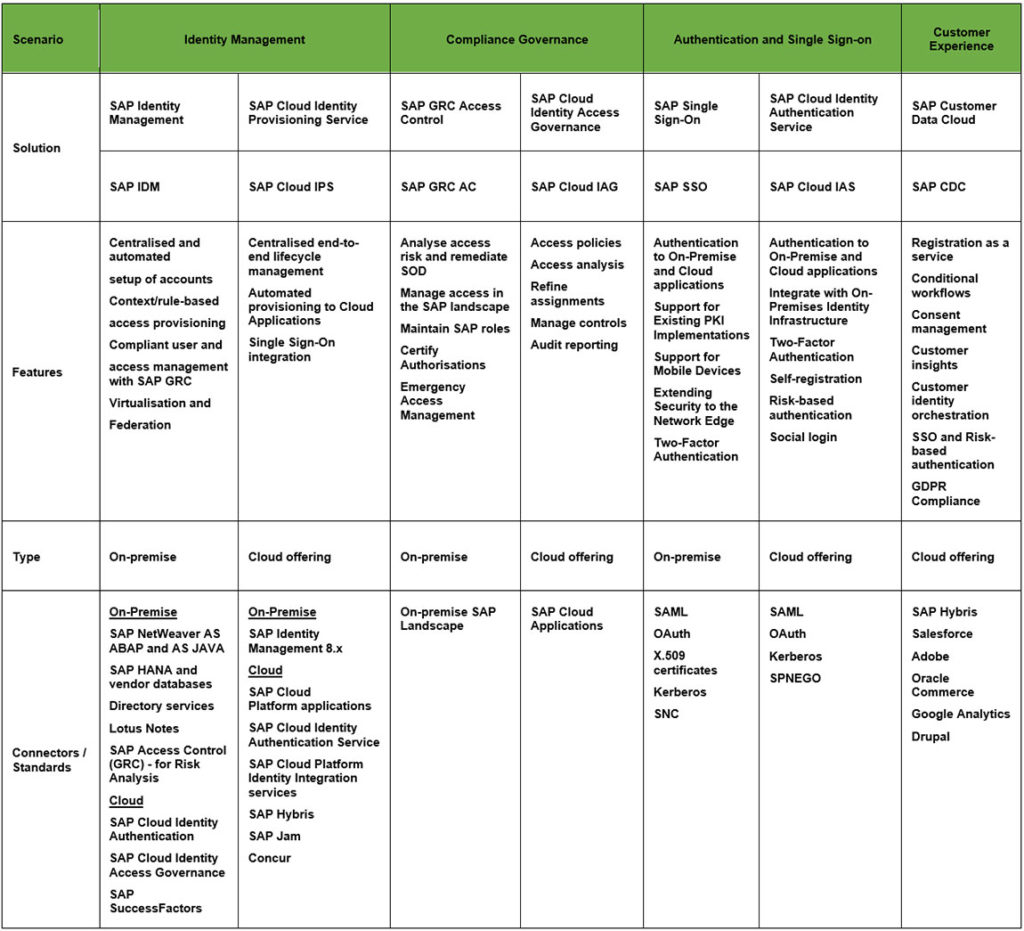
Some of the standard functionalities in SAP security products are provisioning, workflow and password reset replication, whereas the distinct traits are Single Sign-on, Directory Services and application development. A comparative analysis of the attributes of leading products has been presented in the table below.
Decision influencers
Critical to making an informed choice of IAM product is to be aware of which technologies are most likely to support and be cost-effective for your existing or transformational business model. There are several considerations to be accounted for when deciding an appropriate IAM solution usually categorised into four groups.
- Security and Compliance
- Infrastructure
- Business Process
- Financial
Some influential factors that persuade decisions would be:
- Range of standards support
- Ability to customise
- Level of expertise and training required to support the product
- Deployment options (On-Premise or Cloud or Hybrid)
- Support for cloud and mobile applications
- Authorisation policies supported
- Standard connectors to a range of application types
- Multi-Factor Authentication (MFA) support
- Hybrid SSO support
Conclusion
There are a variety of IAM applications available in the market, each having their own capabilities and limitations. These also vary by security standards and compliance. Clients must be careful in choosing the product per requirements as well as existing infrastructure. We started with a comprehensive overview of IAM products, its application fields and decision parameters were outlined.
Identity Management solutions do not only support user and access management but also compliment security, privacy, data protection and compliance requirements as well.
In the next blog, we will dig deeper into each product and how they integrate with each other to solve different IAM use cases.



