Are you working with SAP TM security – experiencing pain in designing the correct worklist access for users and confused with too many POWL tables? This guide explains the SAP TM Security insights, POWL tables co-relations, and their run-time usage. The audience relevant to this document includes but is not limited to security consultants who are working on Personalized Object Worklist (POWL) queries configuration for SAP Transportation Management, SAP Supplier Relationship Management, or SAP Governance, Risk and Compliance solutions.
Topics:
- The detailed process of POWL role creation
- Steps for POWL queries creation (including parameter changes and query settings), query mapping, configuration for role/User. POWL queries and worklists
- Details about the different authorization objects in SAP Transportation Management and it’s usage.
- The ownership and the grey area concerning ownership.
Knowledge Prerequisite:
- SAP application security authorization development
POWL Authorization Development
1. The relevance of POWL queries, Web Dynpro applications, PFCG role & different auth objects in TM
Unlike usual SAP application security authorizations, POWL query access is developed by adding the below elements to the PFCG role:
- BSP Applications
- Authorization Defaults for Transaction codes, TADIR Services, etc.
- Web Dynpro Applications (primary element in POWL/TM authorization development)
- Transaction codes
Below is the relevance of the NWBC screen entities in SAP TM/SRM with the fields/items in the Role PFCG screen. Understanding the significance of the query elements to PFCG role items can make it very easy for security consultants to understand the business requirements and provide the solutions.
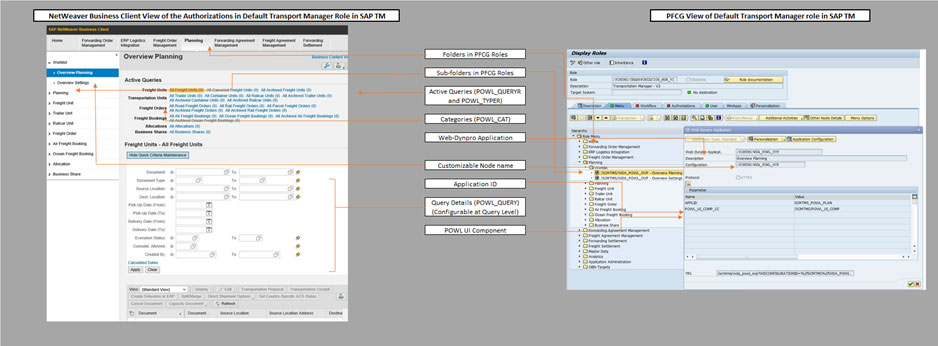
SAP software delivers multiple standard roles for various jobs in SAP TM business processes like Transportation Manager, Planner, and Dispatcher, etc. However, not all these jobs are relevant to all businesses. If they are, the standard Role would still need heavy authorization data maintenance as, by default, they are not maintained.
SCTS – ‘Transport Management Solution’ is the authorization class that holds all the TM relevant auth objects, including critical ones like – T_TM_ALL, T_TORACT, T_TORNODE, T_TOR*, and T_TRQ*.
Let’s look at practical usage information about these auth objects that cannot be found in SU21.
| Class | Auth Object | Info about auth object’s usage |
|---|---|---|
| SCTS | T_TM_ALL | This authorization is analogous to SAP_ALL; but within the TM process scope. If a user has 63 activity for this auth object, system supersedes all the authorization restrictions within the TM scope and provides the access to user. |
| SCTS | T_TORACT & T_TORNODE | There are multiple document types and master data items in the TM system. Although SAP software provides explicit auth objects for regulating access to these items, T_TORACT & T_TORNODE are used to control specific business actions that a user can take on any TM document or master data item. |
| SCTS | T_TOR* & T_TRQ* | This set of authorization objects can be used to regulate the access for various TM documents like freight order, forwarding order based on type, and category. |
| AAAB | CA_POWL | In simple terms, this authorization object helps you regulate user access for a query ‘views’. Changes to the views like creating new queries/categories and editing queries/categories can be controlled using this auth object. |
2. Role development process for POWL access provisioning
2.1 Role development
Task: Web Dynpro Application addition in roles and role generation
Task Ownership: SAP Security Consultants
The entities (T-code, WDA, BSP Appln.) are added to the role like transaction codes. While addition, few more details are to be maintained depending on the kind of access needed, based on business requirements. We can also define and modify SU24 checks for Web Dynpro applications to achieve desired control, with respect to certain parameter.
Steps:
1. Add the required Web Dynpro Application, modify the description to suit the node name, and select/add the relevant configuration ID.
2. Few more parameters can be added and set: Parameters like CHANGE_MODE and APPLID for worklist nodes etc. depending on the requirement.
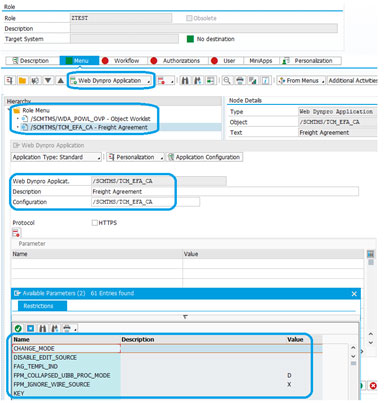
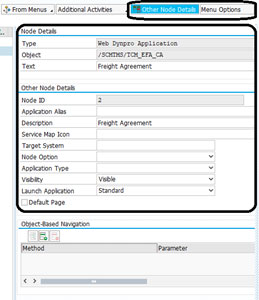
3. We can also add BSP application and authorization defaults (they provide access for the required tcode from NetWeaver Business Client screen)
4. Once we add all the required Web Dynpro applications, tcodes, etc. generate the role authorization profile as usual.
5. ‘Object Worklist type’ Web Dynpro applications need more configuration in POWL tables for providing access to the relevant queries.
2.2 POWL Table configuration
Task: Updating config tables – POWL_QUERYR & POWL_TYPER, or POWL_QUERYU & POWL_TYPEU
Task Ownership: SAP Security/GRC Consultants
There are multiple tables to be updated to provide access for a required POWL Query or Worklist through a role. Table details are as below,
| POWL_CAT | Define Categories with the required descriptions |
|---|---|
| POWL_QUERY | Queries can be defined/modified. Custom queries can be created using predefined POWL Types. The created query can be configured with the help of parameters and customising settings based on business requirements |
| POWL_QUERYR | Defines the relation between Query and Role for an application, using category. This table is used widely because of the ease of defining access to jobs and roles. |
| POWL_QUERYU | Defines the relation between Query and User for an application, using category. This table is NOT used as it is not feasible to define access levels based on the User. |
| POWL_TYPE | Defines the relationship of Query type with the Feeder class. |
| POWL_TYPER | Defines the relation between POWL type and Role for the application. This table is used widely because of the ease of defining access to jobs and roles. |
| POWL_TYPEU | Defines the relation between POWL type and the User for the application. This table is NOT used as it is not feasible to define access levels based on the User. |
2.3 Custom POWL query creation
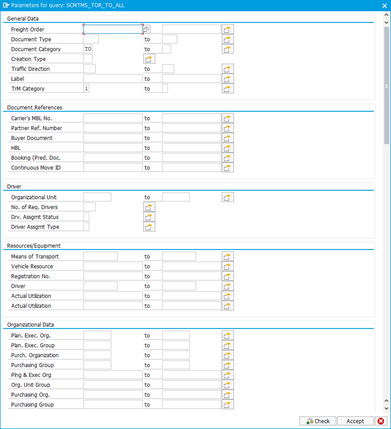
Task: Creation of new queries in POWL_QUERY table Task Ownership: Grey Area – SAP Security Consultants or Relevant SAP Functional Consultant or ABAP Consultants (TM/SRM) Steps- Execute Tcode POWL_QUERY and click on New Entries. Select the POWL Type ID, depending on the type of query you need to create.
- Use Query Parameters and Query Settings options to define and configure the query behaviour.
- Query parameters would be pulled-in depending on the POWL type ID used to define the query.
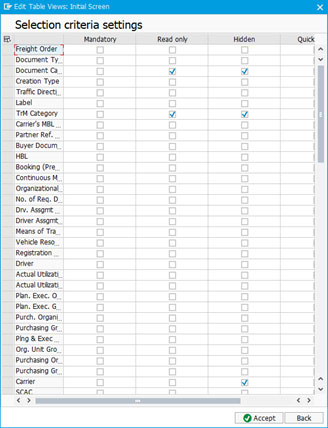
- Query settings can be used for settings including – mandatory field, read-only fields, hidden fields, quick search field visibility, etc.
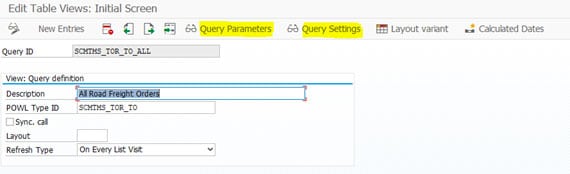
3. POWL Tables / Fields relevance
| Tcode | Table | Talks About | Fields | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
Tcode | Table | Talks About | Fields | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Query ID | POWL Type ID | Category | Application | Role | User | Feeder Class | Relevant Description | Refresh Type | Category Seq No. | Query Seq No. | Tab Seq No. | |||
| POWL_CAT | POWL_CATEGORY | Category Definition - Category Text and Description | x | x | ||||||||||
| POWL_QUERY | POWL_QUERY | POWL Query Definition - Query Text, type of Query and Parameter setting/values | x | x | x | x | ||||||||
| POWL_QUERYR | POWL_QUERY_ROL | POWL Query - Role Assignment Relationship - Role, POWL Query, Application ID and Category For the mentioned Role, Query belongs to relevant Application and should be placed in specified Category in NetWeaver Business Client | x | x | x | x | x | x | x | x | ||||
| POWL_QUERYU | POWL_QUERY_USR | POWL Query - User Assignment Relationship - User, POWL Query, Application ID and Category For the mentioned User, Query belongs to relevant Application and should be placed in specified Category in NetWeaver Business Client | x | x | x | x | x | x | x | x | ||||
| POWL_TYPE | POWL_TYPE | POWL Type Definition - Query Type belongs to this Feeder Class | x | x | x | |||||||||
| POWL_TYPER | POWL_TYPE_ROL | POWL Type - Role Assignment Relationship - Role, POWL Type and Application ID For the mentioned Role, POWL type belongs to this Application | x | x | x | x | ||||||||
| POWL_TYPEU | POWL_TYPE_USR | POWL Type - User Assignment Relationship - User, POWL Type and Application ID For the mentioned User, POWL type belongs to this Application | x | x | x | x |
The above table shows the common fields across the POWL config tables, making it easier to understand how the POWL table configuration enables the query/worklist access. It is not necessary to maintain ALL these tables; the tables to maintain depends upon the approach used for authorization design and POWL configuration (User-based or Role-based)
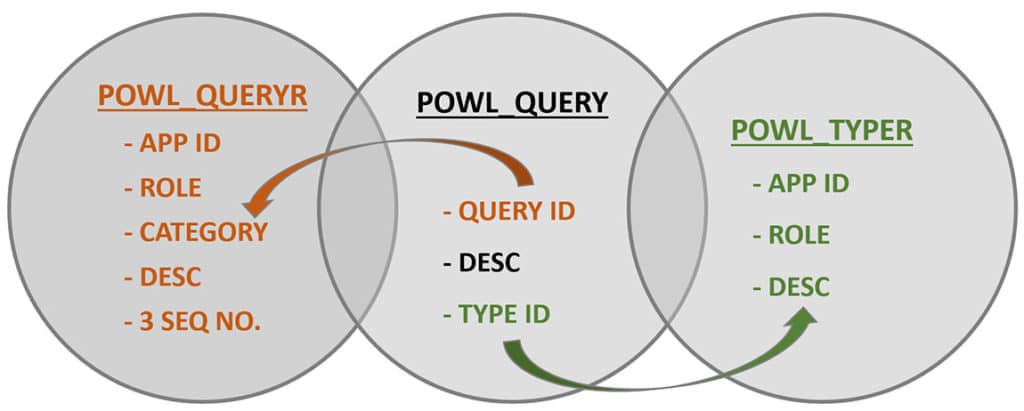
The below graphic shows how entries in config tables POWL_QUERYR & POWL_TYPER use data from query definition is maintained in table POWL_QUERY; when an NWBC page with a worklist is loaded.
Conclusion
Additional information can be found in the ‘Security Guide for SAP TM.’



